Cyber Compromise Assessment
Our Cyber Compromise Assessment provides organisations with fast, independent insight into hidden breaches and security gaps. Unlike routine audits, this Breach Assessment is designed to uncover advanced threats, unauthorised access, and dormant compromises that traditional tools often miss.
Uncover hidden breaches and gain actionable insights into your network’s exposure with a comprehensive threat analysis —powered by just one day’s worth of your firewall logs.

Register Your Interest
Why This Assessment Matters
In today’s rapidly evolving threat landscape, cyber attacks are advancing faster than most businesses can keep up. Many remain unaware of hidden breaches and the real risks they face daily. By harnessing advanced threat intelligence, CyberStash empowers organizations to uncover these threats and gain critical insights into the cyberattacks targeting their systems.
850,000
New Malicious IP Addresses Launched Every Day
30-50 Million
Malicious Domains
At Any Instance
8 Million
Phishing Attacks
Every Day
How It Works
Share Your Firewall Logs
After you register your interest, you will be asked to simply share one day’s worth of firewall traffic logs with our team We’ll handle the rest! The logs can be in firewall-native format or in CSV format.
The logs must contain the following fields:
- Event Timestamp
- Source and Destination IP Addresses
- Destination Port
- Direction
- Action (Allow or Deny)
In-Depth Threat Analysis
Our platform harnesses the power of up to a billion threat intelligence indicators to thoroughly analyze your logs, exposing hidden breaches and attacks lurking within your network. We scrutinize both inbound and outbound traffic to high-risk infrastructures, identifying critical breaches that your current defenses fail to detect—uncovering the blind spots that could leave your organization vulnerable.
Receive a Detailed Report
Within 5 business days, you’ll receive a detailed report that identifies the risks we’ve uncovered, along with expert recommendations to close those gaps and fortify your defenses.
Complementary Report Briefing
Optionally, you can book a follow-up call with one of our cybersecurity experts to review the findings and explore how you can address your security gaps.
Outcomes
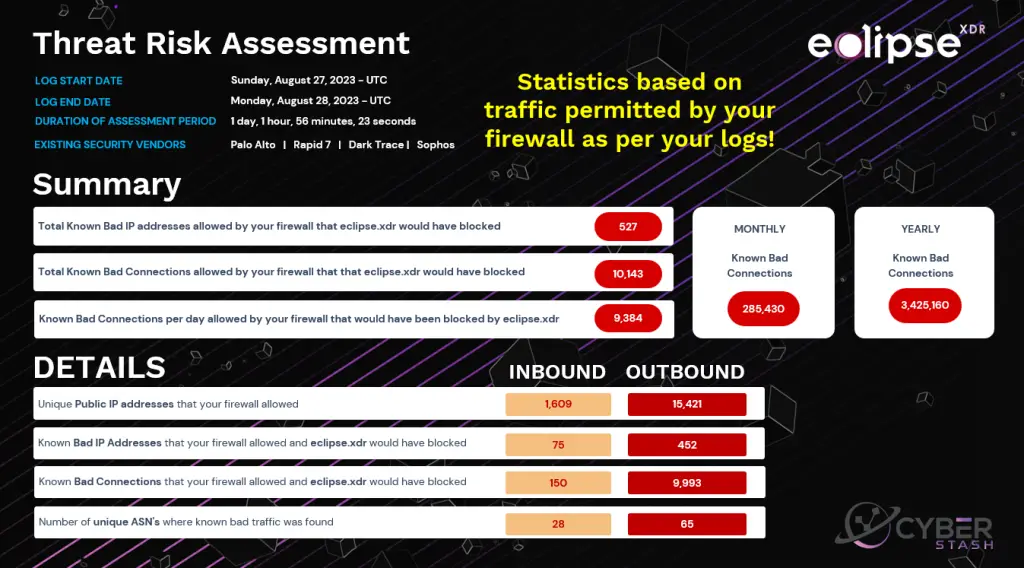
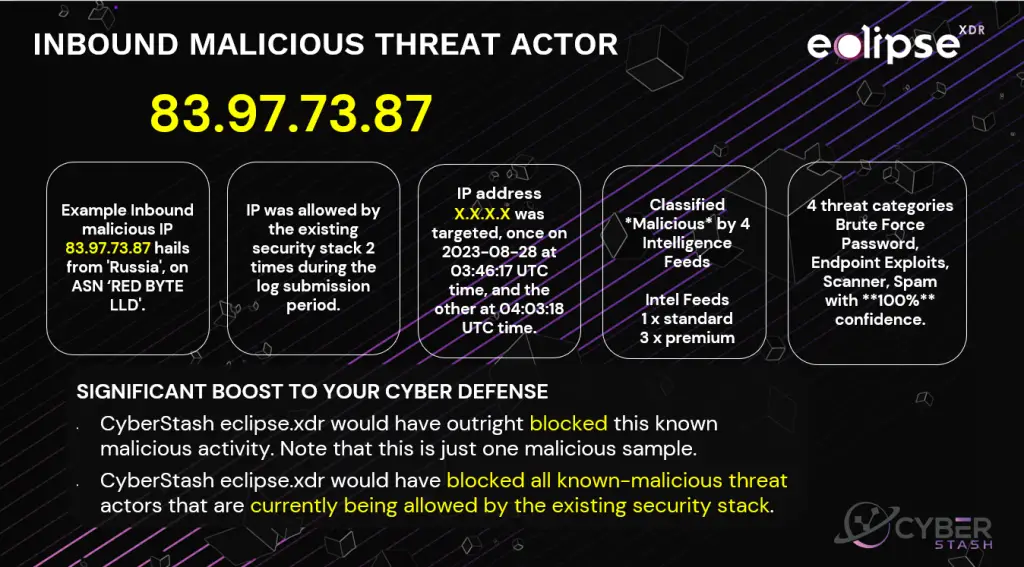
Get Your Complimentaty Assessment
Register Your Interest!
Click the button and fill out the form.
CyberStash will then contact you with additional intructions.
Why CyberStash?
We leverage a wide array of threat intelligence indicators to deliver insights on the threats and attacks facing your organization.
We conduct thorough audits of all traffic flows in and out of your organization, identifying attacks and uncovering previously undiscovered threats.
We can proactively mitigate business impact by actively hunting for, detecting, and preventing sophisticated attacks that bypass current defenses.