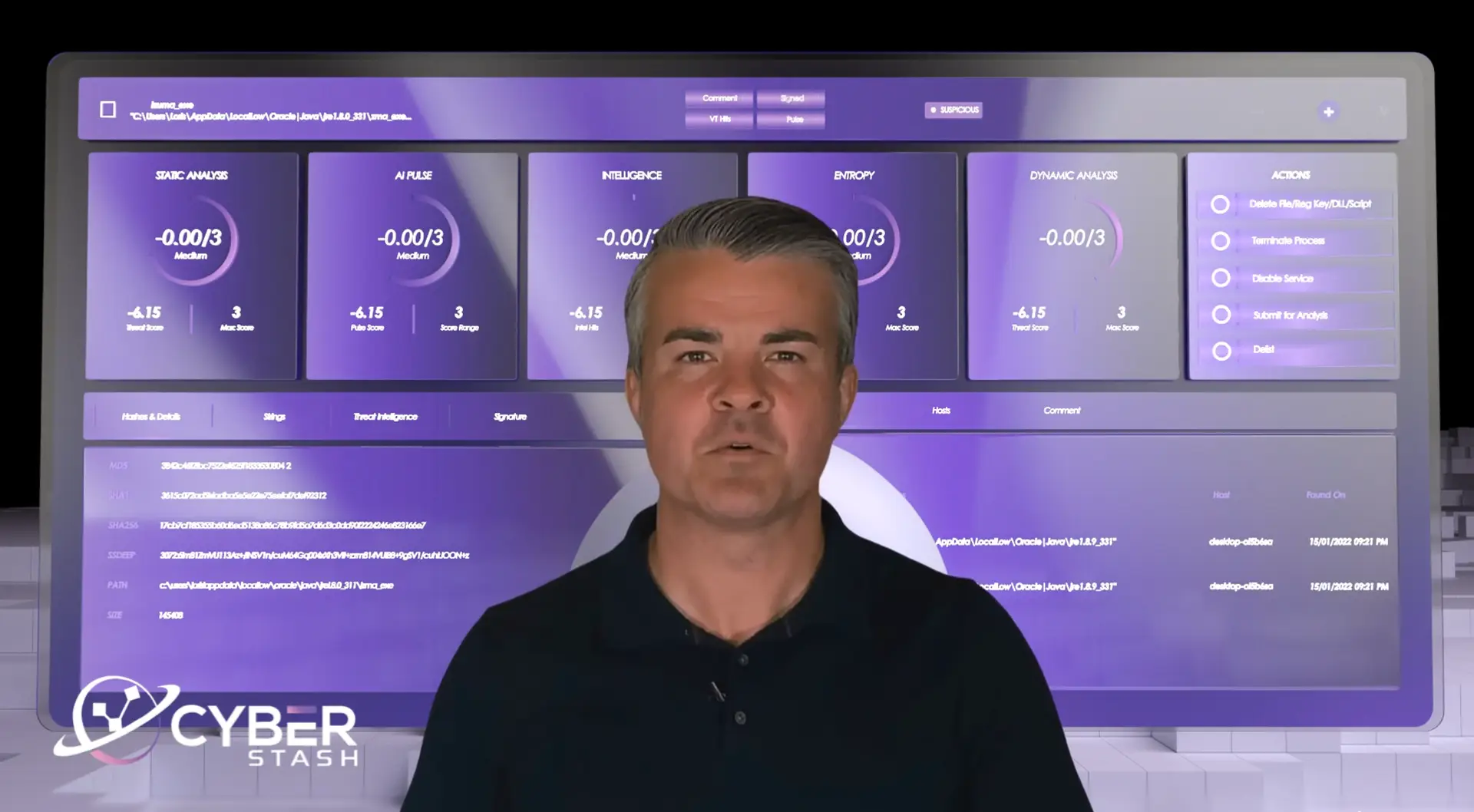
Unfiltered Cyber Security Insights
Scan with Your Phone to Stay Ahead of Threats

Subscribe to Security Advisories
Stay Ahead of Cyber Threats Get timely security advisories crafted by CyberStash experts. Receive practical insights, emerging threat updates, and actionable steps you can use right away to strengthen defences and reduce risk — so you’re always ahead of attackers.

Join Our Next Cybersecurity Webinar
Stay Ahead of Cyber Threats Hear directly from experts on the latest attack techniques and defence strategies. See real-world demos, learn proven countermeasures, and walk away with practical tactics you can apply immediately to improve your organisation’s resilience.

Download the X-in-XDR Whitepaper
Stay Ahead of Cyber Threats Understand what XDR really means for your business and why traditional tools leave gaps. This whitepaper shows how to close those gaps, measure outcomes, and make smarter security investments — insights every IT and security manager can put to use.