
Managed Vulnerability Management Service
Managed vulnerability management that reduces exposure before attackers exploit it — across endpoints, cloud, SaaS, and the external attack surface.
CyberStash delivers managed vulnerability management as a fully managed service, continuously identifying, prioritising, and remediating risk across endpoints, cloud, SaaS, and external attack surfaces. Powered by Qualys and led by experienced security analysts, we reduce exposure and attack surface before vulnerabilities are exploited — not after a breach.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
End-to-End Managed Vulnerability and Exposure Management
We design, deploy, manage, monitor, and report on vulnerability and exposure risk across your environment.
The result is reduced cyber risk, stronger compliance outcomes, and clear audit assurance.
Design
Design the vulnerability management architecture and operating model aligned to business risk and compliance requirements.
Deploy
Rapidly deploy and configure the platform across endpoints, cloud, SaaS, and external assets with minimal disruption.
Manage
Fully manage or co-manage vulnerability, patch, and remediation operations in alignment with your internal teams, processes, and change controls.
Monitor
Continuously monitor and prioritise critical vulnerabilities and exposure risk, while ensuring platform health and data quality operate as expected.
Report
Deliver clear, executive-ready reporting aligned to risk, compliance, and audit requirements.
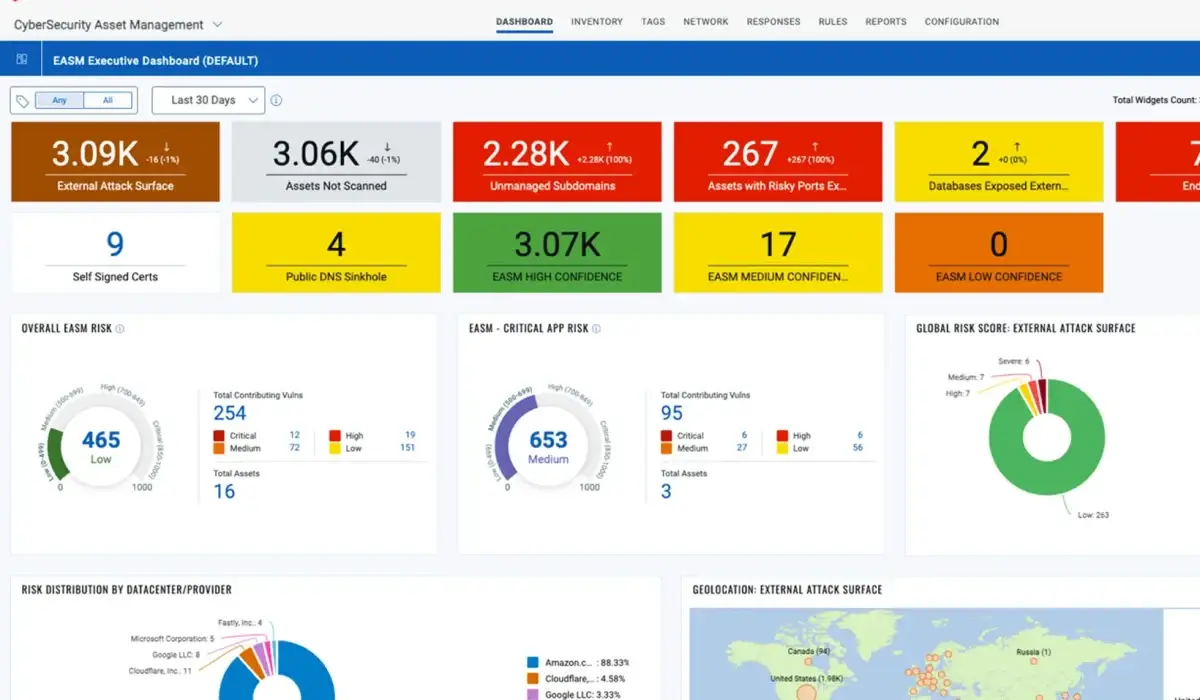
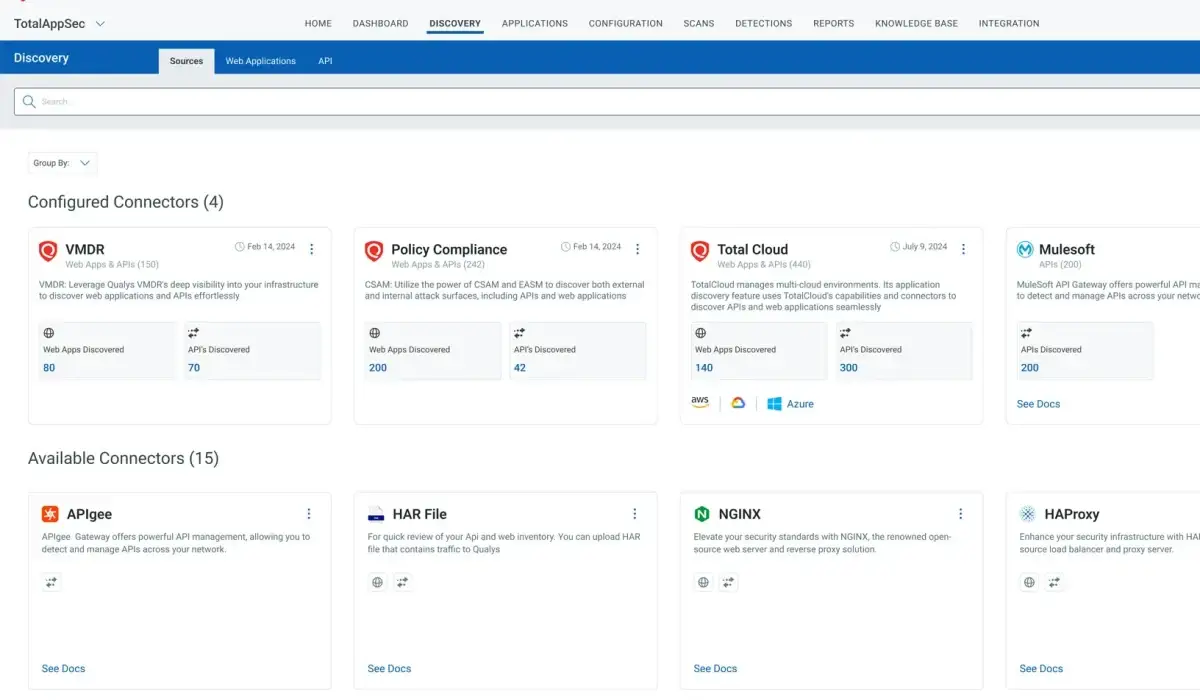
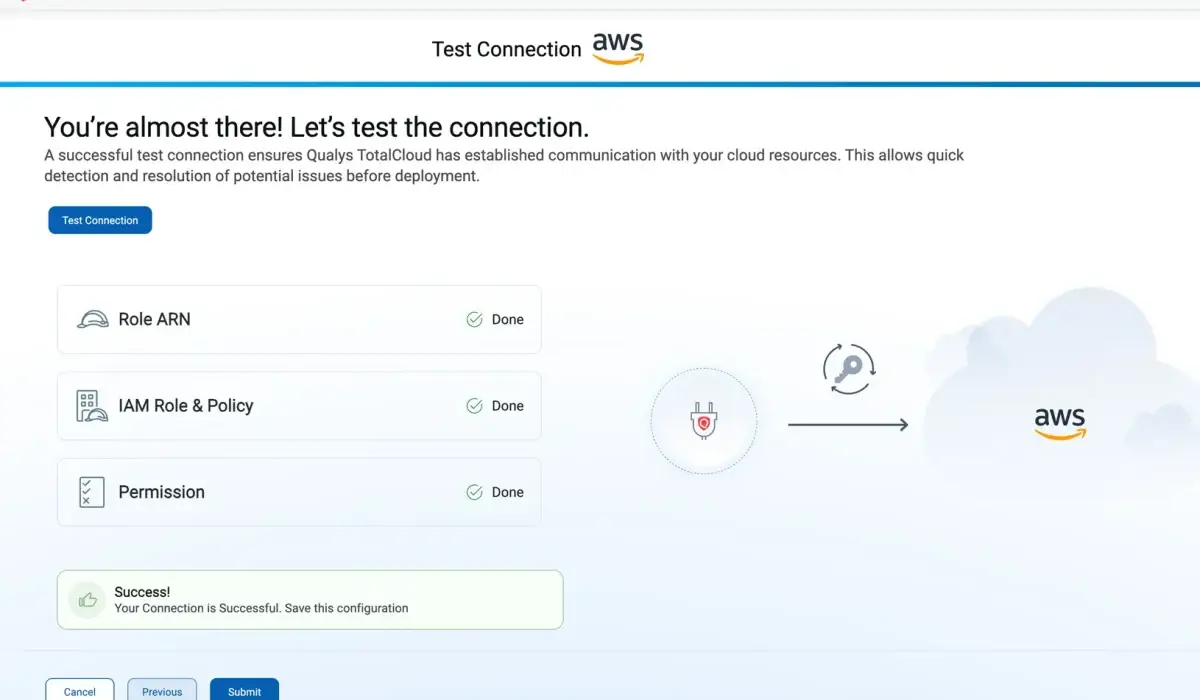

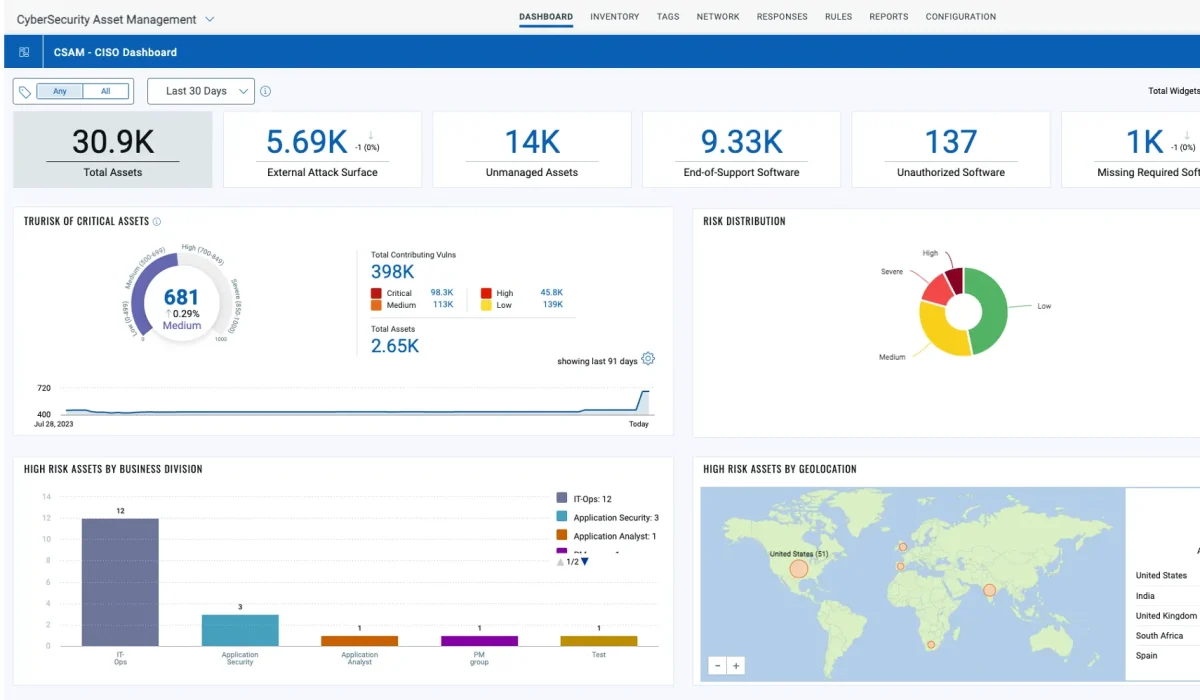
Managing Vulnerabilities and Exposure to Support Compliance and Audit Readiness.
CyberStash delivers vulnerability and exposure management through five integrated service modules, each addressing a critical source of cyber risk. Together, they provide continuous visibility, prioritisation, remediation, and assurance across your on-premises, cloud, SaaS, and external attack surface.
Vulnerability Management (VMDR)
Continuously identify, assess, and prioritise vulnerabilities across all assets using agent-based and network-driven visibility, aligned to real-world threat context and business risk.
Patch & Remediation Management
Reduce exposure by coordinating and managing patching and remediation across Windows, macOS, and Linux environments, ensuring critical vulnerabilities are addressed efficiently and safely.
External Attack Surface Management
Discover and manage internet-facing assets attackers can see, including web applications and APIs, identifying unknown, unmanaged, or forgotten systems that increase breach and compliance risk, aligned to OWASP Top 10 principles.
Cloud Security Posture Management
Identify cloud misconfigurations and security gaps across AWS, Azure, and Google Cloud that increase exposure, supporting secure cloud operations and ongoing compliance alignment.
SaaS Security Posture Management
Strengthen the security of SaaS platforms such as Microsoft 365, Google Workspace, and Salesforce by identifying risky configurations, excessive access, and compliance drift across critical business applications.
Key Business Benefits
CyberStash’s managed vulnerability and exposure management service delivers measurable risk reduction while strengthening compliance and audit outcomes. Each benefit is designed to reduce operational burden, improve visibility, and provide assurance across complex enterprise environments.
Reduced Cyber Risk
Identify and remediate the vulnerabilities that matter most by prioritising real-world exploitability, exposure, and business impact. This reduces attack surface and lowers the likelihood of breaches caused by known and preventable weaknesses.
Stronger Compliance And Audit Readiness
Maintain continuous alignment with frameworks such as ISO 27001 and the Essential Eight through structured remediation, evidence-backed reporting, and consistent controls. Auditors gain clear visibility into vulnerability treatment decisions, not just scan results.
Operational Efficiency And Reduced Burden
Offload day-to-day vulnerability, patch, and remediation management to experienced security specialists, delivered as a fully managed or co-managed service. Your internal teams spend less time chasing findings and more time on strategic initiatives.
Unified Visibility Of What Puts You At Risk
Gain a single, consolidated view of vulnerability and exposure risk across endpoints, networks, cloud platforms, SaaS applications, and external-facing assets. This eliminates blind spots and ensures consistent risk management across hybrid and multi-cloud environments.
Service Delivery Options
Every organisation has a different level of internal capability and appetite for operational ownership. Our service tiers allow you to choose the level of involvement that best fits your team — from deployment support to fully managed Zero-Trust enforcement.
Deployment Only
For organisations that want vulnerability management established correctly from day one, but will operate it internally.
CyberStash designs and deploys the vulnerability and exposure management architecture, configures coverage across endpoints, cloud, SaaS, and external assets, and establishes initial risk and compliance baselines. Ownership of day-to-day operations is then transitioned to your internal team.
Includes:
- Vulnerability and exposure management architecture design
- Platform deployment and initial configuration
- Asset coverage setup (agents, network-based discovery, cloud & SaaS connectors)
- Baseline risk profiling and prioritisation logic
- Compliance-aligned configuration (ISO 27001, Essential Eight)
- Knowledge handover and documentation
Best suited for:
Mature security teams with the capability and capacity to operate vulnerability management internally.
Deploy & Co-Manage
For organisations that want expert oversight and risk prioritisation, while retaining internal control of patching and remediation execution.
CyberStash designs, deploys, and co-manages the vulnerability and exposure management platform alongside your team. We take ownership of platform operation, risk prioritisation, and compliance alignment, while your internal teams retain responsibility for patching and remediation execution. CyberStash provides continuous oversight, escalation, and advisory support to ensure remediation efforts stay aligned to risk and audit requirements.
Includes everything in Deployment Only, plus:
- CyberStash-managed vulnerability and exposure platform operations
- Continuous risk-based prioritisation and validation of critical findings
- Client-owned patching and remediation execution
- CyberStash-led escalation of critical vulnerabilities and exposures
- Advisory support for remediation planning, exceptions, and risk acceptance
- Ongoing tuning of coverage, prioritisation logic, and platform configuration
- Periodic posture reviews and health checks
Best suited for:
Teams that want to retain hands-on control of patching while relying on expert oversight to prioritise risk, guide remediation, and support compliance outcomes.
Fully Managed Service
For organisations that want reduced risk and compliance outcomes without operational overhead.
CyberStash takes full responsibility for the ongoing operation of vulnerability and exposure management. From continuous monitoring and prioritisation to patch and remediation coordination and audit-ready reporting, we operate as an extension of your security team.
Includes everything in Deploy & Co-Manage, plus:
- End-to-end vulnerability and exposure management operations
- Continuous prioritisation of critical vulnerabilities and exposures
- Full patch and remediation management (orchestration and oversight)
- Ongoing platform health monitoring and optimisation
- Executive, risk, and compliance-ready reporting
- Direct access to CyberStash security specialists without escalation friction
Best suited for:
Organisations seeking predictable outcomes, reduced internal effort, and strong risk and audit assurance.
Trusted and Certified to the Highest Standards
CyberStash is independently certified to ISO 27001 and SOC 2, proving our commitment to the highest standards of security, compliance, and trust.

